The Story OF Jump Box
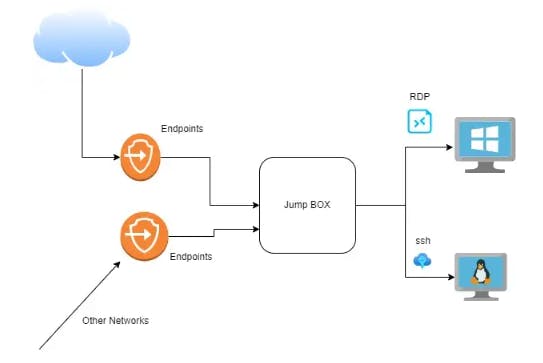
Imagine that there are resources in Azure, such as Linux or Windows virtual machines, and that your environment has multiple copies of each. Typically, we use SSH for Linux and RDP for Windows. Now that you want to connect them to the internet, the jump box is a good idea to prevent them from becoming potentially publicly accessible or open to numerous different network endpoints. A jump box is a network system that allows users to access and operate devices in the different security zone.
Azure Bastion
For situations like the above, we can design our own jump box, which could be a virtual machine. But then there’s the issue of securing that, port checking, and zero-day vulnerabilities. We most likely require multiple jump boxes for scalability, resilience, load balancing, and a number of other factors. The managed jump box service is the main benefit that Azure Bastion is providing for us.

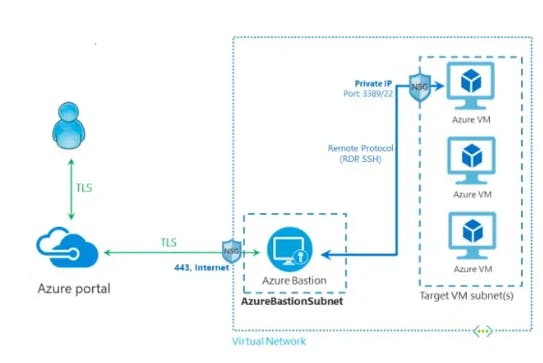
Azure Bastion is a service that you install and use to connect to a virtual machine via your browser and the Azure portal. The Azure Bastion service is a fully managed PaaS service that you deploy within your virtual network. It provides secure and seamless RDP/SSH access to your virtual machines from the Azure portal via TLS. When you connect through Azure Bastion, your virtual machines do not require a public IP address, an agent, or any special client software.
Bastion provides secure RDP and SSH access to all VMs in the virtual network in which it is installed. Using Azure Bastion prevents your virtual machines from exposing RDP/SSH ports to the outside world while still allowing secure RDP/SSH access.
In order to access to Azure resources that you do not want direct connections to, Azure Bastion provides a quick, simple, secure, and economical solution. It is a PaaS alternative that truly replaces jump box servers and is an agentless solution. For ingress and egress connections, you can restrict access to Azure Bastion by configuring a specific Network Security Group (NSG).